Introduction
APIs (Application Programming Interfaces) power modern digital applications, facilitating smooth and efficient communication between diverse systems. However, many APIs have restrictions such as limited access, missing documentation, or encryption, making data retrieval a challenge. Reverse Engineering API techniques allow developers and businesses to analyze, understand, and access data from APIs that are otherwise restricted.
In this blog, we explore how Reverse Engineering API tools can help unlock restricted data, the methods used, real-life applications, and key statistics to showcase its impact.
Understanding Reverse Engineering API
Reverse Engineering an API involves analyzing an existing API to uncover its structure, endpoints, and functionalities—especially when official documentation is unavailable or incomplete. This technique allows businesses to integrate APIs more effectively, extract valuable data, and bypass unnecessary restrictions.
Why Reverse Engineer an API?
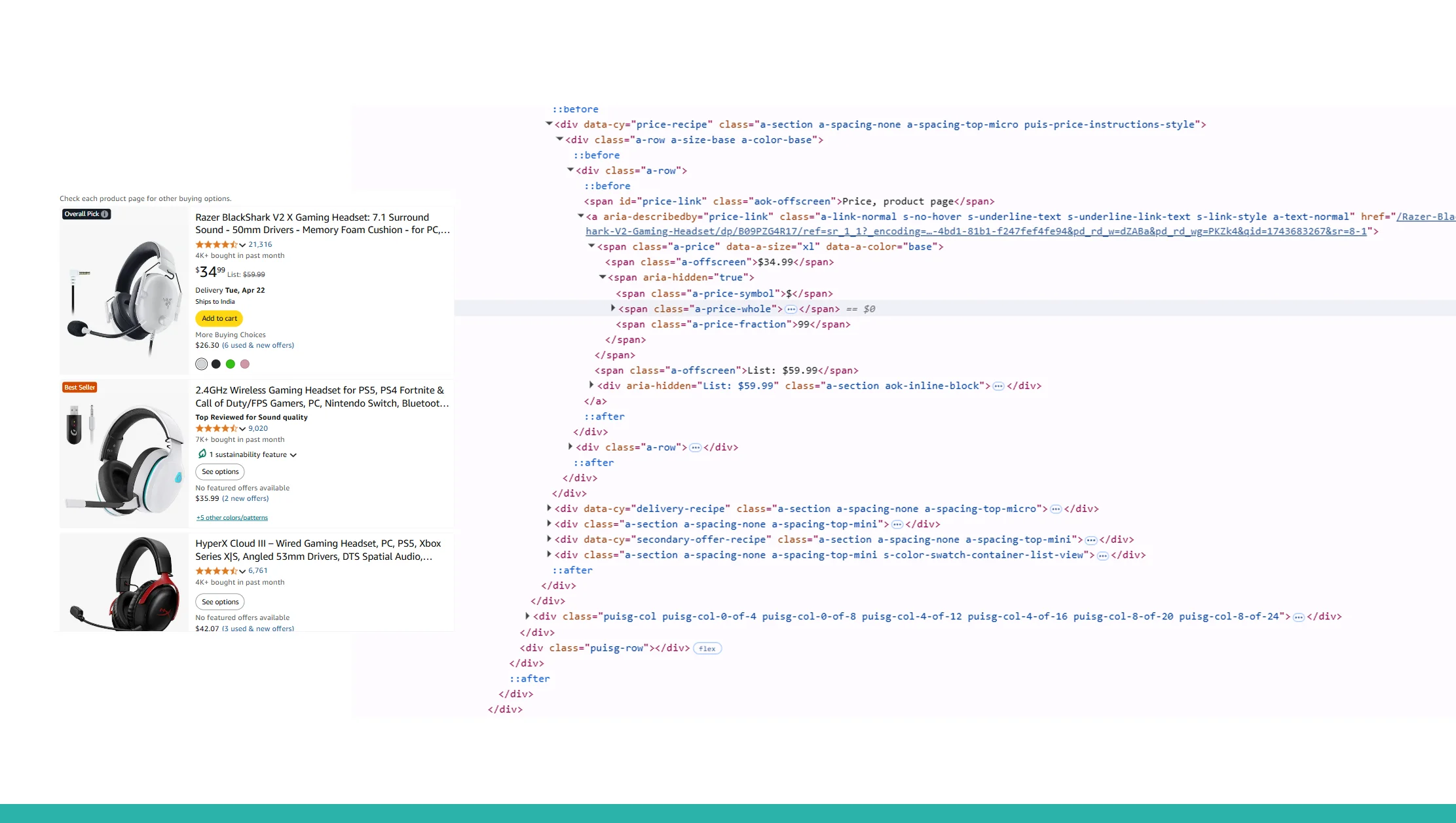
1. Access Undocumented or Restricted Data
Many APIs have hidden or restricted endpoints that are not publicly documented. Reverse engineering helps uncover these endpoints, providing access to valuable insights and hidden functionalities.
2. Improve API Integration in Applications
Without proper documentation, API integration can be challenging. By analyzing API requests and responses, developers can optimize integration, ensuring seamless functionality in their applications.
3. Debug and Troubleshoot API Failures
When an API malfunctions, debugging can be difficult without official documentation. Reverse engineering helps identify errors, understand response patterns, and troubleshoot issues effectively.
4. Enhance Automation by Bypassing Manual Interactions
Some APIs require unnecessary manual interactions for authentication or data retrieval. By studying the API’s request structure, businesses can automate processes and enhance efficiency.
5. Recover Lost API Documentation
If an API’s documentation is outdated, incomplete, or missing, reverse engineering helps recreate it. This ensures that developers have a clear reference for future projects and integrations.
Reverse engineering APIs is a powerful technique for businesses and developers looking to unlock hidden functionalities, optimize integration, and enhance automation. It helps bypass unnecessary restrictions, improve API performance, and extract valuable data for business growth.
Unlock hidden data and optimize API integration with Reverse Engineering API tools!
Start exploring today!Methods to Reverse Engineer an API
There are multiple approaches to Reverse Engineering API, depending on the level of security, encryption, and data restrictions. Below are the most commonly used methods:
1. Reverse Engineer an API Using Postman

Postman is a popular tool for API testing and analysis. It can be used to inspect API calls, capture responses, and test different parameters.
Steps:
1. Monitor network activity in the browser (using DevTools or Postman Interceptor).
2. Capture API requests and responses.
3. Analyze headers, parameters, and response structure.
4. Replicate and modify requests to test API behavior.
Use Case:
A fintech company needed access to real-time transaction data from a payment gateway API that lacked proper documentation. Using Postman, developers reverse-engineered the API calls and successfully integrated the payment system into their platform.
2. Reverse Engineer an API Using Proxy

Using a proxy tool like Burp Suite, Charles Proxy, or Fiddler allows developers to intercept and inspect network traffic between an application and an API.
Steps:
1. Configure the proxy tool to intercept API traffic.
2. Analyze HTTP/S requests and responses.
3. Modify API calls to test different parameters.
4. Extract and decode encrypted data if necessary.
Use Case:
An e-commerce business needed customer insights from a competitor’s mobile app API. By setting up Charles Proxy, they intercepted API traffic and identified endpoints that provided product pricing, reviews, and stock levels.
3. Reverse Engineering Encrypted APIs

Some APIs use encryption techniques to secure data, making it difficult to access raw data directly. Reverse engineering such APIs requires advanced techniques like decryption, SSL pinning bypass, and payload analysis.
Steps:
1. Identify the encryption method (AES, RSA, etc.).
2. Use SSL proxy tools to analyze encrypted traffic.
3. Apply decryption techniques to extract raw data.
4. Modify and test API requests based on findings.
Use Case:
A cybersecurity firm analyzed a suspicious mobile application using Reverse Engineering Encrypted APIs to uncover hidden user tracking mechanisms. They successfully decrypted the API requests and found unauthorized data sharing practices.
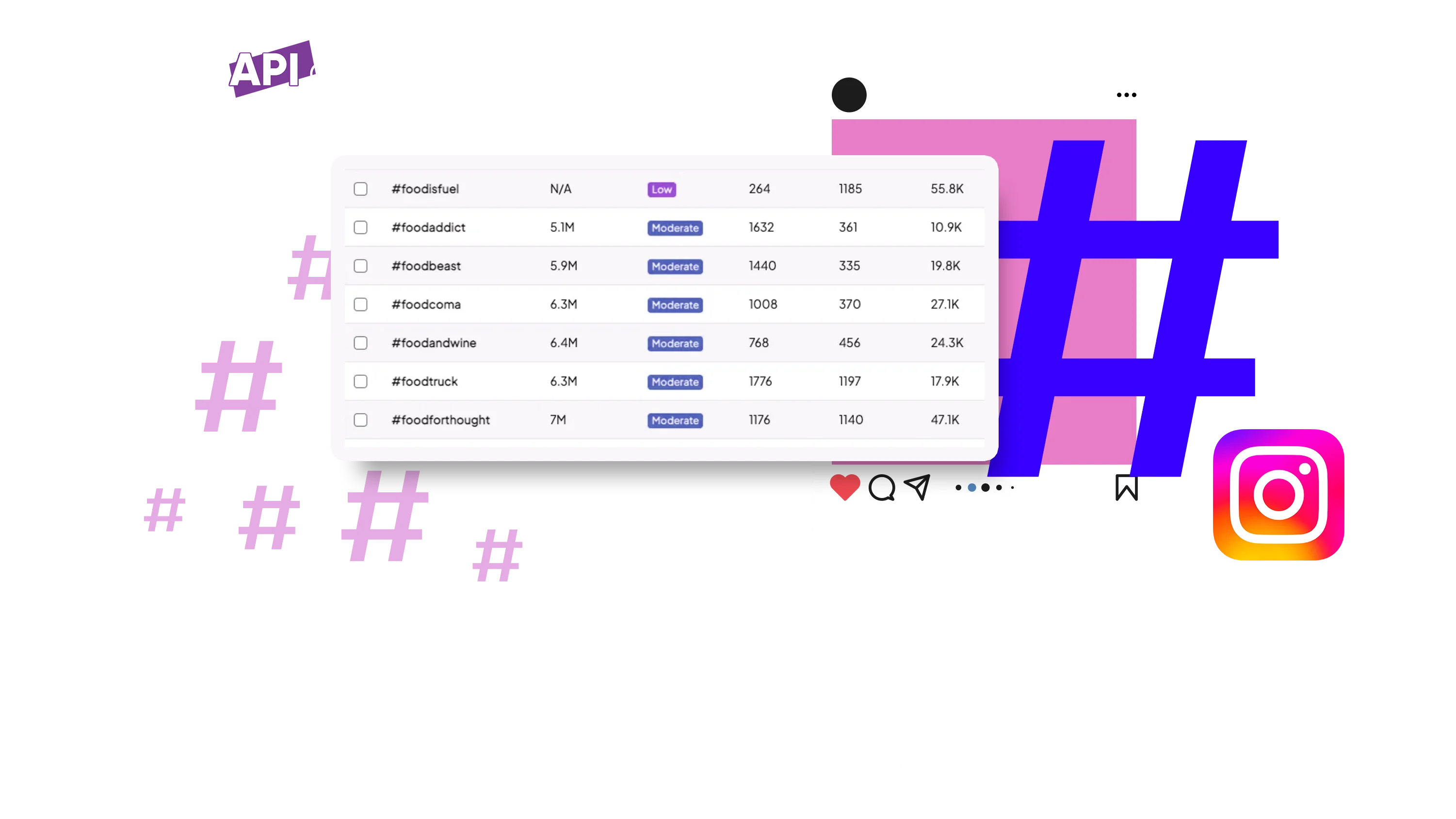
Key Statistics on API Reverse Engineering
| Statistic | Insight |
|---|---|
| 80% of web traffic | Comes from APIs, making API analysis crucial. |
| 40% of APIs | Lack proper documentation, requiring reverse engineering. |
| 75% of businesses | Use APIs for automation and data retrieval. |
| 60% of mobile apps | Rely on third-party APIs, some of which are undocumented. |
Discover powerful Reverse Engineering API methods to unlock data, enhance API integration, and automate workflows!
Start exploring today!Real-Life Applications of Reverse Engineering API
Reverse Engineering an API is widely used across industries for competitive analysis, legacy system integration, cybersecurity, and more. By leveraging Reverse Engineering API tools, businesses can extract data, improve API integration, and enhance security.
1. Competitive Analysis
Businesses can analyze competitor APIs to gather crucial data, such as pricing strategies, customer reviews, and product trends.
Example: Expedia reverse-engineered airline APIs from American Airlines and Delta to monitor fare fluctuations and implement dynamic pricing strategies in real time.
2. Legacy System Integration
Many enterprises rely on outdated APIs that lack proper documentation, making API integration challenging. Reverse Engineering APIs helps modernize these systems.
Example: Mayo Clinic reverse-engineered an old patient management API to seamlessly integrate it with their new Epic EHR system, improving data accessibility for healthcare providers.
3. Cybersecurity & Ethical Hacking
Security researchers and ethical hackers use Reverse Engineering API techniques to identify vulnerabilities and prevent data breaches.
Example: Cybersecurity firm Palo Alto Networks reverse-engineered a banking API from Wells Fargo, discovering a critical security flaw that exposed user transaction details. This led to a patch that strengthened customer data protection.
How to Reverse Engineer an API?
- Reverse Engineer an API Using Postman – Capture and analyze API requests to understand endpoints.
- Reverse Engineer an API Using Proxy – Use tools like Burp Suite or Charles Proxy to inspect encrypted traffic.
- Reverse Engineering Encrypted APIs – Decrypt API requests and responses to analyze hidden data structures.
Reverse Engineering APIs is a powerful method to gain a competitive edge, enhance cybersecurity, and modernize legacy systems. Using Reverse Engineering API tools like Postman, Burp Suite, and Charles Proxy, businesses can uncover hidden functionalities and optimize their API integration strategies.
Why Choose Real Data API?

Real Data API ensures businesses access accurate, real-time data for better decision-making, automation, and competitive analysis. Unlike static datasets, Real Data APIs deliver live updates, improving API integration and workflow efficiency.
Key Benefits:
- Real-Time Insights – Stay ahead with continuously updated data.
- Seamless API Integration – Easily connect with applications using Reverse Engineering API tools.
- Enhanced Security – Utilize Reverse Engineering Encrypted APIs to analyze secure data channels.
- Business Scalability – Automate processes and optimize performance.
With Reverse Engineering API techniques, businesses can extract valuable real-time insights, making Real Data APIs a game-changer for growth.
Conclusion
Reverse Engineering API techniques empower businesses to access, analyze, and integrate data from restricted or undocumented sources. Whether using Reverse Engineering API tools, leveraging Postman or Proxy-based techniques, or decrypting secured APIs, these methods provide valuable insights and seamless API integration solutions.
If you need assistance in Reverse Engineering API for your business, contact Real Data API today to unlock new possibilities and gain a competitive edge!
.webp)
.webp)